I just obtained Verizon Fios service again at-last (after a few unbearable weeks on RCN). Verizon sent a nice new gigabit router (Actiontec MI424WR rev 3) to go along with it.
So, here’s where things get interesting. I set up the network myself. I changed the DHCP configuration, moved the subnet, changed the SSID and made it hidden, added WPA-2 PSK using a 64-character ASCII key generated by GRC, disabled remote administration, locked down the router, etc.
Next, after confirming everything was working, and modifying my TCP settings to achieve the rated speeds, I logged on to the myVerizon site, to set up automatic payments.
That’s when I saw it:
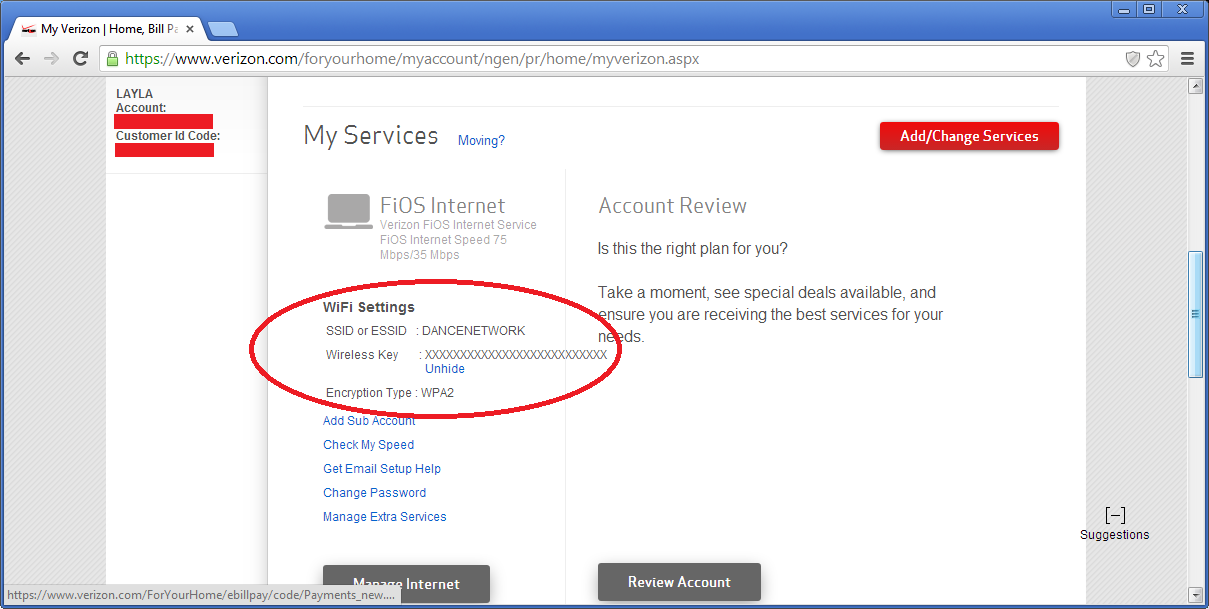 That’s right: the myVerizon website, out on the real internet, knows my custom SSID, knows that I’m using WPA2, and knows my custom WPA2 Pre-Shared Key. Clicking un-hide does indeed work.
That’s right: the myVerizon website, out on the real internet, knows my custom SSID, knows that I’m using WPA2, and knows my custom WPA2 Pre-Shared Key. Clicking un-hide does indeed work.
Verizon/Actiontec have a backdoor in the MI424WR router. I wonder what else it’s exporting for the benefit of Verizon / NSA? (oh, I jest :-/)
How difficult would it be for a malicious user to exploit this backdoor to potentially gain unauthorized access to my Router or my LAN? It would take more investigation to be sure (e.g. is the backdoor exposed via a low-level protocol on the Coax/Fiber, or, is it exposed through TCP to the entire WAN/Internet)?
But no matter the outcome of further investigations, this is already a direct breech of security, leaking, at a minimum, private settings and keys, and also adding vulnerable surface area to the wrong side of the Router.
When all it takes to reset everything to factory settings for the average brain-dead customer who has forgotten their password or key is to hold the “reset” button for 15 seconds, what possible <reasonable> justification for this level of intentional security hole is there?
I suppose the obvious answer is that, to Verizon’s bottom line, it does not matter. The public doesn’t care about security, so Verizon doesn’t feel any need to provide it to them. They choose to provide convenience for their customer service department instead. And the tiny number of customers such as myself that they may lose because of this issue don’t even compare to the noise against their bottom line. Le Sigh.
Update — a screenshot to show that I’ve disabled remote management:
It appears that the router uses:
- TR-69+ Remote Management
- http://en.wikipedia.org/wiki/TR-069

This protocol, according to Wikipedia, is supposed to be initiated by the device. It’s supposed to be used to remote-configure devices.
I configured my router manually, before even connecting it to the Coax/WAN, so this protocol shouldn’t have been invoked. If Verizon is using this protocol to share my passwords without my consent, it would seem to be an abuse of the stated purpose.
Alas, maybe that’s what the “+” in “TR-69+” stands for? 🙁
